
Blockchain technology is like a three-trick pony. It essentially combines three slightly clumsy computer tricks to mimic decisions that a human administrator routinely makes. The difference is that, if done correctly, the computer can perform some of these decisions with great speed, accuracy and scalability. The peril is that, if done incorrectly, the computer can propagate an incorrect outcome with the same stunning efficiency.
1: The Byzantine General’s Dilemma
A scenario first described in 1982 at SRI International models the first trick. This problem simulation refers to a hypothetical group of military generals, each commanding a portion of the Byzantine Army, who have encircled a city that they intend to conquer. They have determined that: 1. They all must attack together, or 2. They all must retreat together. Any other combination would result in annihilation.
The problem is complicated by two conditions: 1. There may be one or more traitors among the leadership, 2. The messengers carrying the votes about whether to attack or retreat are subject to being intercepted. So, for instance, a traitorous general could send a tie-breaking vote in favor of attack to those who support the attack, and a no vote to those who support a retreat, intentionally causing disunity and a rout.
See also: Can Blockchains Be Insured?
A Byzantine Fault Tolerant system may be achieved with a simple test for unanimity. After the vote is called, each general then “votes on the vote,” verifying that their own vote was registered correctly. The second vote must be unanimous. Any other outcome would trigger a default order to retreat.
Modern examples of Byzantine Fault Tolerant Systems:
The analogy for networks is that computers are the generals and the instruction “packet” is the messenger. To secure the general is to secure the system. Similar strategies are commonplace in engineering applications from aircraft to robotics to any autonomous vehicle where computers vote, and then “vote on the vote.” The Boeing 777 and 787 use byzantine proof algorithms that convert environmental data to movements of, say, a flight control surface. Each is clearly insurable in a highly regulated industry of commercial aviation. So this is good news for blockchains.
2: Multi-Key Cryptography
While the Byzantine Fault Tolerant strategy is useful for securing the nodes in a network (the generals), multi-key cryptography is for securing the packets of information that they exchange. On a decentralized ledger, it is important that the people who are authorized to access information and the people who are authorized to send the information are secured. It is also important that the information cannot be tampered with in transit. Society now expends a great deal of energy in bureaucratic systems that perform these essential functions to prevent theft, fraud, spoofing and malicious attacks. Trick #2 allows this to be done with software.
Assume for a moment that a cryptographic key is like any typical key for opening locks. The computer can fabricate sets of keys that recognize each other. Each party to the transaction has a public key and a private key. The public key may be widely distributed because it is indiscernible by anyone without the related private key.
Suppose that Alice has a secret to share with Bob. She can put the secret in a little digital vault and seal it using her private key + Bob’s public key. She then sends the package to Bob over email. Bob can open the packet with his private key + Alice’s public key. This ensures that the sender and receiver are both authorized and that the package is secured during transit.
3: The Time Keeper
Einstein once said, the only reason for time is so that everything doesn’t happen at once. There are several ways to establish order in a set of data. The first is for everyone to synchronize their clocks relative to Greenwich, England, and embed each and every package with dates of creation, access records, revisions, dates of exchange, etc. Then we must try to manage these individual positions, revisions and copies moving through digital space and time.
The other way is to create a moving background (like in the old TV cartoons) and indelibly attach the contracts as the background passes by. To corrupt one package, you would need to hijack the whole train. The theory is that it would be prohibitively expensive, far in excess of the value of the single package, to do so.
Computer software of the blockchain performs the following routine to accomplish the effective equivalent process: Consider for a moment a long line of bank vaults. Inside each vault is the key or combination to the vault immediately to the right. There are only two rules: 1. Each key can only be used once, and 2. No two vaults can be open at the same time. Acting this out physically is a bit of a chore, but security is assured, and there is no way to go backwards to corrupt the earlier frames. The only question now is: Who is going to perform this chore for the benefit of everyone else, and why?
Finally, here is why the coin is valuable
There are several ways to push this train along. Bitcoin uses something called a proof-of-work algorithm. Rather than hiding the combinations inside each vault, a bunch of computers in a worldwide network all compete to guess the combination to the lock by solving a puzzle that is difficult to crack but easy to verify. It’s like solving a Rubik Cube; the task is hard to do, but everyone can easily see a solution – that is sufficient proof that work has been done and therefore the solved block is unique and valid, thereby establishing consensus.
Whoever solves the puzzle is awarded electronic tokens called bitcoin (with a lower case b). This is sort of like those little blue ticket that kids get at the arcade and can be exchanged for fun prizes on the way out. These bitcoins simply act as an incentive for people to run computers that solve puzzles that keep the train rolling.
Bitcoins (all crypto currencies) MUST have value, because, if they did not, their respective blockchain would stop cold.
A stalled blockchain would be the crypto-currency equivalent of bankruptcy. This may account for some amount of hype-fueled speculation surrounding the value of such digital tokens. Not surprisingly, the higher the price, the better the blockchain operates.
While all of this seems a bit confusing, keep in mind that we are describing the thought patterns of a computer, not necessarily a human.
The important thing is that we can analyze the mathematics. From an insurability standpoint, most of the essential ingredients needed to offer blockchain-related insurance products exist as follows.
1. The insurer can identify the risk exposures associated with generals, traitors, locks, vaults, trains and puzzles.
2. The insurer can calculate probability of failure by observing:
- The degree of Byzantine fault tolerance.
- The strength of the cryptography
- The relative value of the coins (digital tokens)
3. The consequences of failure are readily foreseeable by traditional accounting where the physical nature of the value can be assessed, such as a legal contract.
We can therefore conclude that each of the tricks performed by this fine little pony are individually insurable. Therefore, the whole rodeo is also insurable if, and only if, full transparency is provided to all stakeholders and the contract has physical implications.
Markets are most efficient when everyone has equal access to information – the same is essential for blockchains. So much so that any effort to control decentralized networks may, in fact, render the whole blockchain uninsurable. It is fundamentally important that the insurer is vigilant toward the mechanics of the blockchain enterprise that they seek to insure, especially where attempting to apply blockchain to its own internal processes.
Adapted from: Insurance: The Highest and Best Use of Blockchain Technology, July 2016 National Center for Insurance Policy and Research/National Association of Insurance Commissioners Newsletter: http://www.naic.org/cipr_newsletter_archive/vol19_blockchain.pdf


 Anyone who was around in the early 1990’s may remember the mantra of modern globalization was that centralized markets were bad and decentralized markets were good. Fast forward to 2016 and blockchain technology: centralized ledgers are bad decentralized ledgers are good. Does this sound familiar? Blockchain and NAFTA may have a lot in common. The good news is that perhaps this new world is not quite as uncharted as it now appears.
Anyone who was around in the early 1990’s may remember the mantra of modern globalization was that centralized markets were bad and decentralized markets were good. Fast forward to 2016 and blockchain technology: centralized ledgers are bad decentralized ledgers are good. Does this sound familiar? Blockchain and NAFTA may have a lot in common. The good news is that perhaps this new world is not quite as uncharted as it now appears.
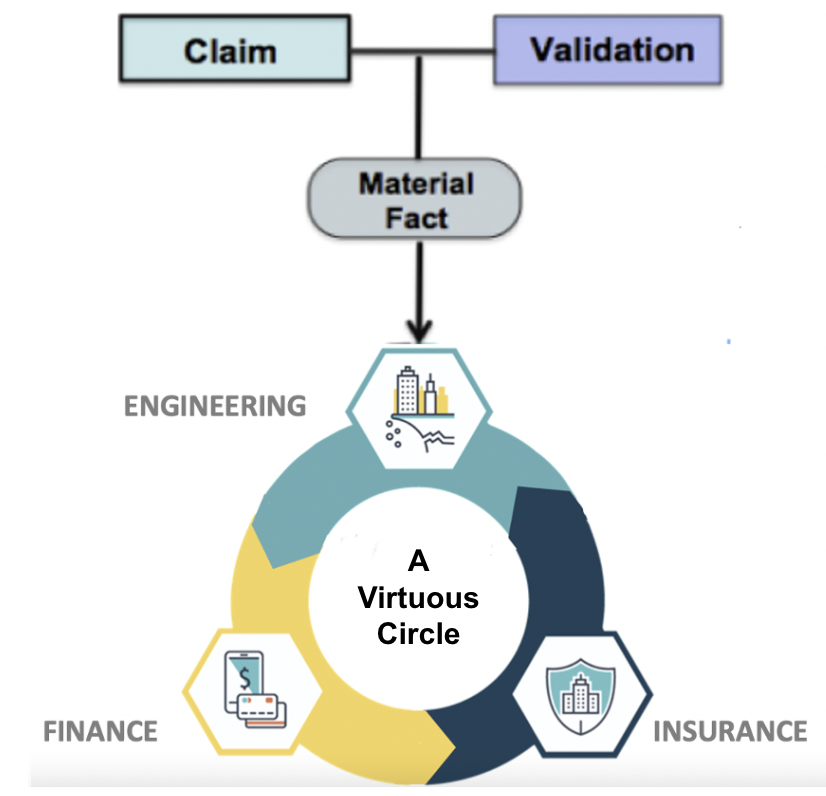
 Are blockchains insurable? This question was posed to us as a topic for presentation by the Center of Insurance Policy and Research, a research arm of the National Association of Insurance Commissioners (CIPR / NAIC)
Are blockchains insurable? This question was posed to us as a topic for presentation by the Center of Insurance Policy and Research, a research arm of the National Association of Insurance Commissioners (CIPR / NAIC)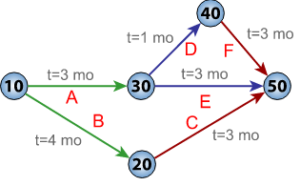 On a critical path.
On a critical path. The hallmark of a great society is the ability to capitalize it’s needs, not it’s arbitrage opportunities. The Highest and Best Use for Blockchain Technology must be to reduce the cost of capital by decentralizing risk, not necessarily money…yet
The hallmark of a great society is the ability to capitalize it’s needs, not it’s arbitrage opportunities. The Highest and Best Use for Blockchain Technology must be to reduce the cost of capital by decentralizing risk, not necessarily money…yet